Hey all, I’ve been having this issue for a while now and troubleshooting has been driving me crazy. Maybe someone more knowledgeable can help figure out what’s going on.
About a week ago I noticed that when using my pihole-unbound DNS server, very specific domains always fail to resolve when previously they would be resolved correctly. It is very particular which domains fail, the vast majority of domains I visit get resolved. The following domains always fail to resolve on any device using pi-hole:
- debian.org
- duck.ai
- arin.net
- energy.gov
- cdc.gov
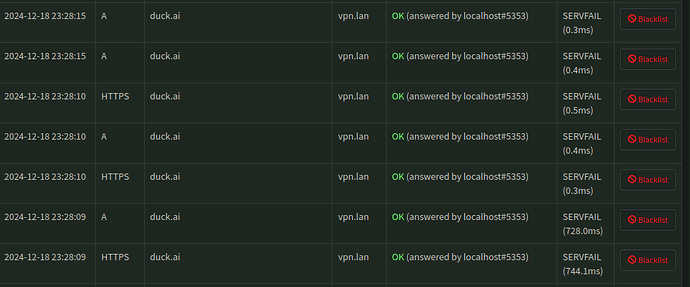
After taking a look at the pihole WebUI’s query log, I noticed that every query that fails to resolve had the same SERVFAIL message in the reply column: (Using duck.ai as the affected domain)
This pointed me to the issue being with Unbound, so I used docker exec to add the following lines to the end of /etc/unbound/unbound.conf to generate a log file:
verbosity: 1
log-servfail: yes
log-replies: yes
log-queries: yes
Here are the contents of said newly created log: (Using debian.org as the affected domain)
[1734580590] unbound[944:0] info: start of service (unbound 1.13.1).
[1734580595] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580596] unbound[944:0] info: generate keytag query _ta-4f66. NULL IN
[1734580597] unbound[944:0] info: validation failure <debian.org. A IN>: No DNSKEY record from 192.36.148.17 for key debian.org. while building chain of trust
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 2.088680 0 39
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 0.000000 1 39
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 0.000000 1 39
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580597] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 0.000000 1 39
[1734580598] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580598] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 0.000000 1 28
[1734580598] unbound[944:0] info: 127.0.0.1 debian.org. A IN
[1734580598] unbound[944:0] info: 127.0.0.1 debian.org. A IN SERVFAIL 0.000000 1 28
[1734580607] unbound[944:0] info: 127.0.0.1 google.com. A IN
[1734580607] unbound[944:0] info: 127.0.0.1 accounts.youtube.com. A IN
[1734580607] unbound[944:0] info: 127.0.0.1 google.com. A IN NOERROR 0.351449 0 55
[1734580607] unbound[944:0] info: 127.0.0.1 accounts.youtube.com. A IN NOERROR 0.144987 0 93
[1734580607] unbound[944:0] info: 127.0.0.1 google.com. AAAA IN
[1734580607] unbound[944:0] info: 127.0.0.1 www3.l.google.com. TYPE65 IN
[1734580607] unbound[944:0] info: 127.0.0.1 google.com. AAAA IN NOERROR 0.030153 0 67
[1734580607] unbound[944:0] info: 127.0.0.1 www3.l.google.com. TYPE65 IN NOERROR 0.038562 0 96
[1734580614] unbound[944:0] info: 127.0.0.1 rr1---sn-vgqsknly.googlevideo.com. A IN
[1734580615] unbound[944:0] info: 127.0.0.1 rr1---sn-vgqsknly.googlevideo.com. A IN NOERROR 0.258469 0 97
Now this is where I’m out of my depth. The line No DNSKEY record from 192.36.148.17 for key debian.org. while building chain of trust is of particular interest to me, as it seems to be where the issue resides, but I’m not experienced enough with unbound or DNSSEC to understand how to solve it, or really what it fully means to be honest.
Here’s what I have already tried in my troubleshooting:
- Verify the CasaOS server date/time/timezone is correct
- Verify the
TZenvironment variable for the container is set to the local timezone - Export config, delete pihole-unbound from CasaOS UI, then reinstall from config
- Verify DNSSEC is NOT enabled in pi-hole
- Inside container, delete
/var/lib/unbound/root.key+ rununbound-anchor(As suggested here)
I haven’t had any luck so far. Any solutions or troubleshooting tips would be greatly appreciated!